Passkeys
Passkeys are, as described by the FIDO Alliance, "a password replacement that provides faster, easier, and more secure sign-ins to websites and apps across a user's devices."
Using passkeys allows for passwordless user sign-up and sign-in, which creates a safer environment for your system's users who don't have to rely on easily exploitable, legacy authentication methods such as passwords.
Passkeys are an industry-accepted and adopted standard, which means that all of your users will be able to use this feature, no matter the hardware they work with. The notable adopters of passkeys include:
- Apple with Apple Passkeys
- Microsoft
While companies can add proprietary features to passkeys, such as iCloud synchronization in Apple Passkeys or Google Password Manager synchronization for Android devices, all of them use the same FIDO standard. This means that enabling passkeys is a simple, one-time operation in Ory.
To learn more about passkeys and see sample flows for different platforms, watch this FIDO Alliance video:
Choose passkey strategy
Ory Network implements a dedicated passkey strategy that improves the ergonomics over using the webauthn strategy for first-factor login. Here is a comparison of the two approaches:
| Webauthn passwordless login | Passkey strategy | |
|---|---|---|
| Discoverable credentials: The browser automatically discovers which credentials the user has stored for the site. | ❌ | ✔︎ |
| Conditional UI: The browser attaches an autofill dropdown to the email field that allows the user to select a passkey. | ❌ | ✔︎ |
| Backwards compatibility: Works for users that have a passkey configured with the WebAuthN strategy. | ✔︎ | ❌ |
Passkeys with the dedicated passkey strategy
Configuration
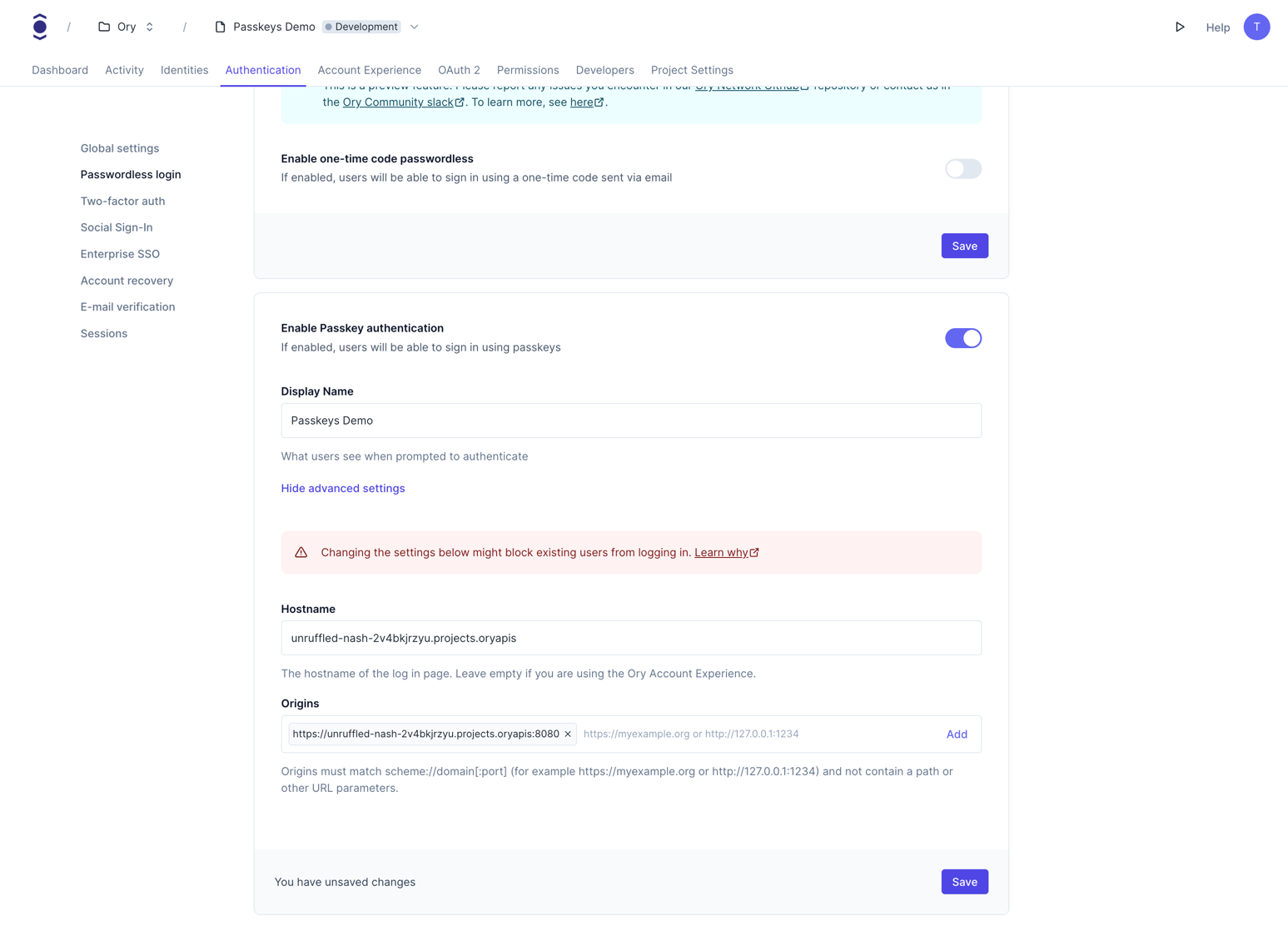
By default, the passkey strategy is disabled. Go to Authentication → Passwordless login in the Ory Console and toggle the switch for Enable Passkey authentication to enable it.
Alternatively, use the Ory CLI to enable the passkey strategy:
- Ory CLI
- Full Config
ory patch identity-config <your-project-id> \
--add '/selfservice/methods/passkey/enabled=true' \
--add '/selfservice/methods/passkey/config/rp/display_name="My Display Name"'
selfservice:
methods:
passkey:
enabled: true
config:
display_name: "My Display Name"
Identity schema
If you want to use a custom identity schema, you must define which field of the identity schema is the display name for the
passkey. If you do not define the passkey.display_name field, the webauthn.identifier will be used as a fallback. If neither
is defined, the passkey strategy will not work.
{
$schema: "http://json-schema.org/draft-07/schema#",
type: "object",
properties: {
traits: {
type: "object",
properties: {
email: {
type: "string",
format: "email",
title: "Your E-Mail",
minLength: 3,
"ory.sh/kratos": {
credentials: {
// ...
passkey: {
display_name: true,
},
},
// ...
},
},
// ...
},
// ...
},
},
}
Passkeys with the WebAuthN strategy
Configuration
To allow using passkeys, enable passwordless login. To do that in the Ory Network, go to
Authentication → Passwordless login in the Ory Console and toggle the switch to enable the feature.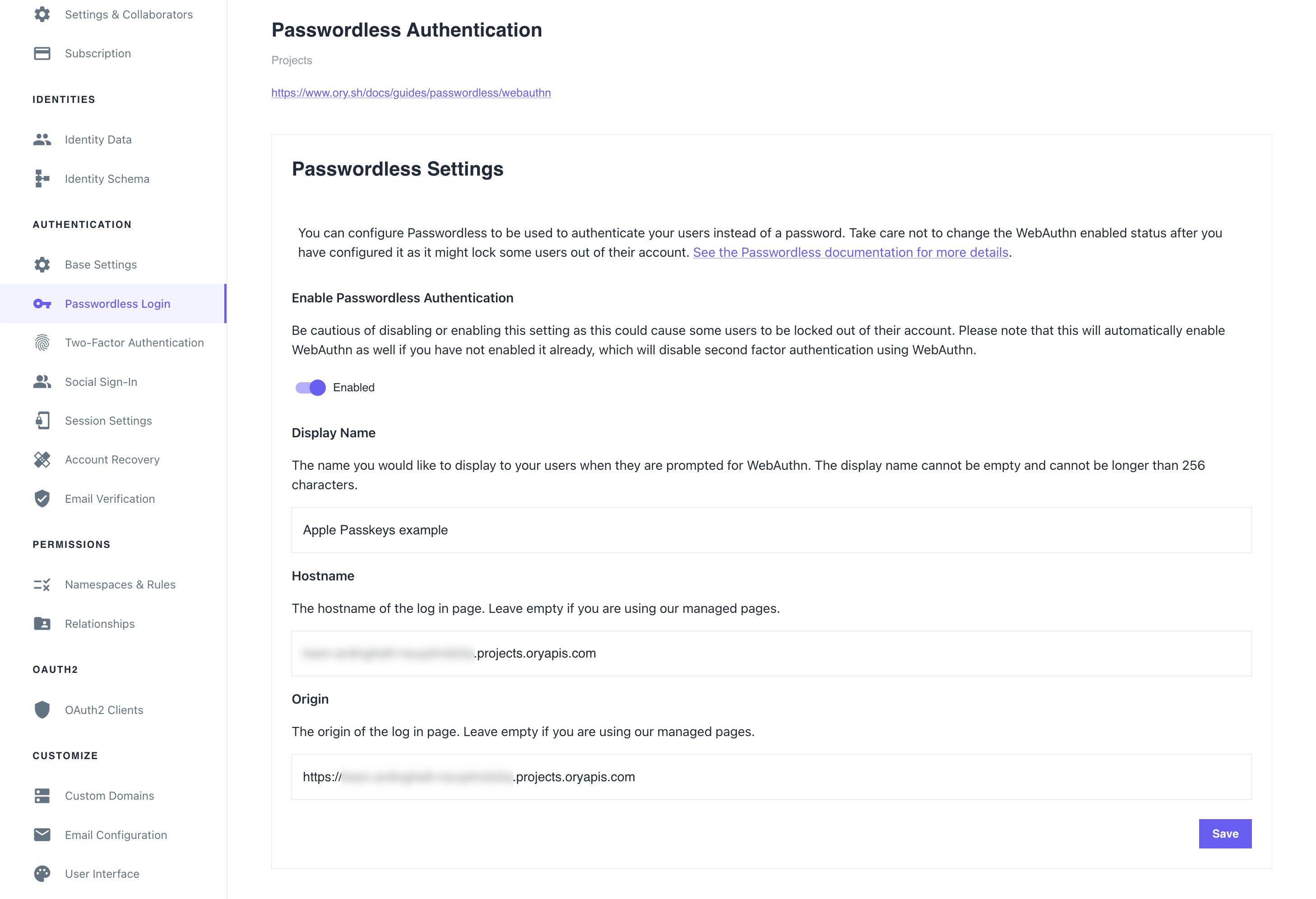
Example
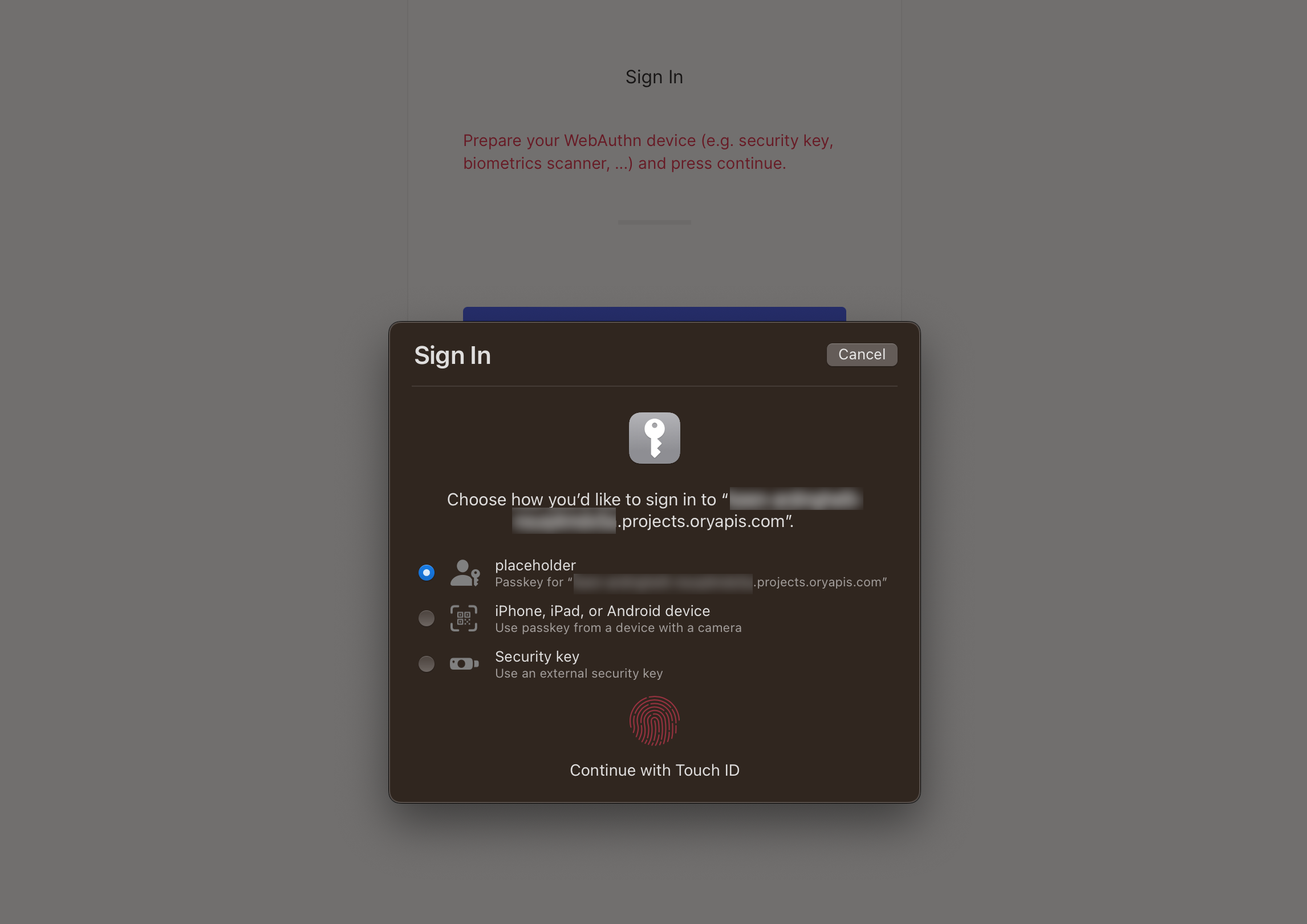
This is a macOS Safari prompt the browser shows when users try to sign in using the passwordless method. The first option allows to use a passkey associated with this account that's stored in the iCloud Keychain of the user that's signed in to iCloud on this device.
The second option allows delegating user authentication to a camera-equipped device. Upon successful authentication, a matching passkey found on the device will be used to sign in.